Secure Your Distributed Workforce with Endpoint Backup
Endpoint Backup is a comprehensive, automatic backup solution that protects your organization's most vulnerable data residing on endpoint devices.
Endpoint Data Protection Reimagined
Endpoint Backup simplifies the complexities of deploying data protection across your entire organization, regardless of size, distribution, or IT sophistication.

Mitigate Data Loss and Breaches
Protect valuable data on employee devices, minimize the risk of data loss and breaches, and quickly restore lost data.
Centralized Management
Easily deploy, configure, and manage backups across dozens, hundreds, or even thousands of endpoints from a single dashboard.

Advanced Security Features
Safeguard laptops from internal and external threats with features like device tracking, legal hold, SSO, and 2FA options.
Protect Your Endpoint Data with Confidence
Don't let the evolving workforce put your organization's data at risk. Implement Endpoint Backup today and enjoy peace of mind knowing your endpoint data is secure and recoverable.

Why Choose Endpoint Backup?
Trusted by Thousands of Businesses Worldwide
Backup Uptime
Data Loss
We provide strategic, transformational, and technical offerings in Endpoint Backup
- Key Features of Endpoint Backup
Endpoint Backup offers a robust set of features to protect your organization's data and ensure business continuity:
Flexible Deployment Options
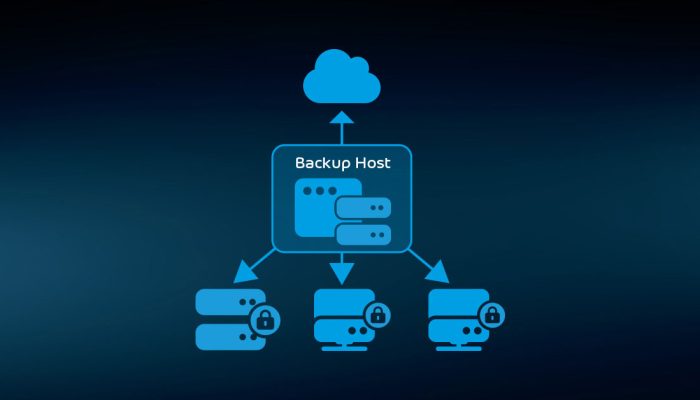
Choose to back up your data to our secure cloud, the public cloud, or on-premise infrastructure.
Global Deduplication
Benefit from powerful, global deduplication of encrypted data, optimizing storage and network efficiency.
Centralized Backup Management
Automate and control backups across the entire company from a single, user-friendly dashboard.
Global Location Tracking
Locate and track lost or stolen endpoint devices, minimizing the risk of data breaches.
Training and Support
Empower your team with comprehensive training and ongoing support to maximize the value of your SharePoint investment.














- Our Straightforward Onboarding Method
Within our organization, we boast a diverse team of technical experts offering extensive managed firewall services. Our onboarding procedure for managed firewall services is swift and user-friendly. Our primary goal is to propel your business forward with precise services, ensuring you achieve the desired outcomes. Below, we outline the process and operations designed to maximize your benefits.
1
Project Initiation
We’ll create a transition strategy and provide dedicated managers to assist you every step of the way.
2
Knowledge Transfer
Intensity will capture your existing operational procedures, protocols, and regulations and assign roles and responsibilities to all our resources.
3
Reverse Knowledge Transfer
We collect feedback from project SMEs to improve knowledge transition from project acquisition.
4
Services Setup
Our experts will set up resources, tools, and protocols in close collaboration with your existing teams and vendors.
5
Service Transition
We take on all responsibilities from your previous vendors in a phased manner to minimize downtime.
6
Handover
Our resources will take care of everything you need with a hassle-free operational flow once the service start date is reached.
Client Testimonials


Frequently Asked Questions
How does Endpoint Backup protect against data loss and breaches?
Endpoint Backup automatically backs up data from employee devices, ensuring that critical information is securely stored and easily recoverable in the event of data loss or a breach.
Can Endpoint Backup be deployed across a large, distributed workforce?
Yes, Endpoint Backup’s silent deployment technology makes it easy to roll out the software across dozens, hundreds, or even thousands of endpoints, regardless of geographic location.
What security features does Endpoint Backup offer?
Endpoint Backup includes advanced security features such as device tracking, legal hold, single sign-on (SSO), and two-factor authentication (2FA) options to protect your data from internal and external threats.
Is Endpoint Backup compliant with industry regulations?
Yes, Endpoint Backup operates a control framework based on adherence to SOC 2 Type 2 standards and supports compliance with several industry-standard regulations, including HIPAA, FERPA, GLBA, and GDPR.
How does Endpoint Backup ensure high performance and minimize network disruption?
Endpoint Backup provides tools to intelligently manage global bandwidth usage, minimizing disruption to network performance while ensuring your data is protected.
Safeguard Your Endpoint Data
with OpenText Cybersecurity
Endpoint Backup is part of OpenText Cybersecurity’s comprehensive suite of solutions designed to help your organization become cyber resilient. Our experts are ready to help you deploy, manage, and optimize your endpoint data protection strategy.
Client results
Explore our success stories to see how we have helped businesses like yours overcome challenges and achieve tangible results.